At some point, the time will come when a system administrator needs to disable user accounts on a Linux system. This can be achieved by Linux nologin technique. Some common reasons for disabling user accounts are due to some suspicious user activity, or perhaps due to a user’s work contract termination.
As far as the overall system security is concerned, it is always a good idea to have only those user logins enabled which are necessary for the system or company to function. This tutorial explores some ways on how to disable user accounts on any Linux distro.
In this tutorial you will learn:
- How to disable user accounts with
nologin - How to disable user account with
falseand other shells - How to disable user accounts with
usermodand/etc/shadow

| Category | Requirements, Conventions or Software Version Used |
|---|---|
| System | Any Linux distro |
| Software | N/A |
| Other | Privileged access to your Linux system as root or via the sudo command. |
| Conventions | # – requires given linux commands to be executed with root privileges either directly as a root user or by use of sudo command$ – requires given linux commands to be executed as a regular non-privileged user |
Disable user accounts via nologin
The nologin shell is located at /sbin/nologin. On some systems, this shell may also be located at
/usr/sbin/nologin. Either way, it’s the same file and will provide the same function.To set a user’s shell to nologin, you can use the usermod command, along with the -s or --shell option, as seen in the syntax below. In this example, we are setting the shell for user linuxconfig.
# usermod linuxconfig -s /sbin/nologin
From then on, when the user tries to login, they will see the following message:
This account is currently not available.
Disable user account with false and other shells
There are more shells available that function similarly to /sbin/nologin. The most well known one is probably /bin/false. This isn’t really a “shell,” but just a file that will return false and exit instantly.
This works perfectly fine for disabling a user account, but doesn’t have the advantage of issuing a message when the user tries to login. For this reason, the /sbin/nologin file will normally be the ideal way to disable a user account (that is, if you wish to do so by changing the user shell).
To set a user’s shell to false, you can use the usermod command in the same syntax as we saw above.
# usermod linuxconfig -s /bin/false
You could also use /bin/true instead, which will do the same thing. To see more shells that your system has available, execute the following command.
$ cat /etc/shells
Disable user accounts by editing /etc/shadow
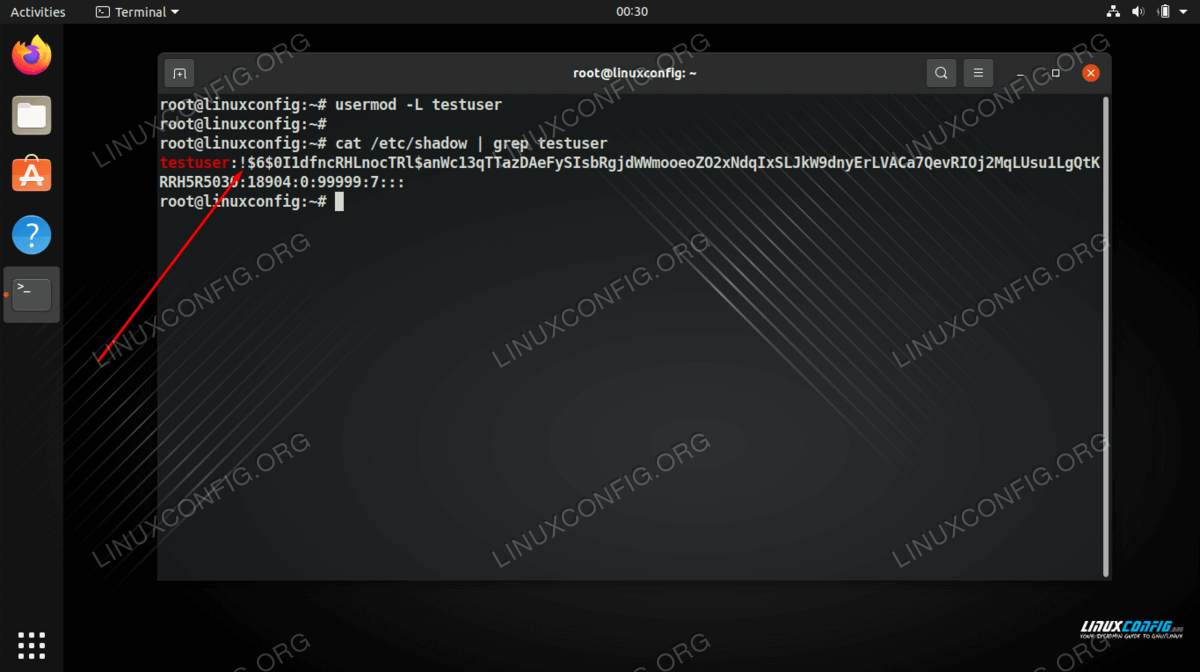
You can lock a user’s account with the usermod command and -L option.
# usermod -L testuser
The only thing this does is add an ! exclamation point to the beginning of the user’s encrypted password in the /etc/shadow file. You can observe this yourself by viewing the /etc/shadow file after disabling a user account.
# cat /etc/shadow | grep testuser
To unlock the user account, which simply removes the exclamation point from the beginning of the user’s password in /etc/shadow, use the -U option with the usermod command.
# usermod -U testuser
Closing Thoughts
In this linux nologin guide, we saw several methods that can be used to disable a user account on a Linux system. This included editing the user’s shell to
nologin or false, which are popular choices, or just changing the user’s encrypted password in /etc/shadow so they would never be able to login. Use whichever method you find most appropriate for your system administration situation.
No hay comentarios:
Publicar un comentario